With hackers getting more creative, UCC (unified communications and collaboration) systems are increasingly at risk of unwanted intrusion. In recent weeks, Microsoft has shown that these systems still have their fair share of vulnerabilities, no matter how secure they claim to be.
As has Slack's team collaboration software - which experienced some issues during the Pandemic, along with others like Zoom. The video conferencing giant faced a lot of backlash following instances of Zoombombing toward the beginning of the Pandemic.
Cyber Security in a Digital Era, McKinsey, 2020
I wanted to learn more about these systems and the risks users encounter daily. One Dr. Joseph Williams, Partner, Global Cybersecurity Practice, Infosys Consulting, lent me further insight into the matter, sitting down for a recent interview.
If you aren't familiar with Infosys Consulting, it is a management and IT consulting firm with offices in 18 countries across the Americas, Asia Pacific, and Europe.
With over 20 years of experience working at Microsoft and in various roles in the world of cyber security and academia - Williams has a decent amount of clout to speak on the matter. During our time chatting, Williams extended some worthwhile cautions to enterprises and the employees that spin the wheels within these organizations.
The goal here is to avoid intrusions like the ones we have seen in recent weeks, all in hopes of protecting sensitive consumer and company-wide data.
One of the first blunders IT leaders make, Williams told me, is putting so much trust in vendor claims about the security of their platforms. For the most part, he noted that hackers have figured out that UC platforms: because of their ubiquity in the enterprise they have become an attractive mark.
Hacking, a Crime of Opportunity
Think of it as a crime of opportunity, Williams shared, if a hacker understands there is an easy way in, they will likely choose to expose any weakness they find. He continued, further telling me that:
"Internal IT tends to place too much trust in believing UCC system vendor assertions about platform security."
He believes that these folks also tend to forget the magnitude of the 2020 Zoom breach and all the work done by cyber security researchers to publicize vulnerabilities in platforms like GoToMeeting, Teams, Zoom, and Webex over the years.
Since then, Williams said, hackers have found more creative ways to intrude upon intentional privacy. He believes that: one of the easiest ways to gain access to private systems is to purchase existing credentials on the Dark Web from initial access brokers (IAB).
Cyber Security in a Digital Era, McKinsey, 2020
It can also (be achieved) through phishing or social engineering, which remain two of the most popular methods for hackers to gain ungranted access to various UCC systems. "That gets them access to the platform and any data available to that user," Williams cautioned.
"Very clever hackers have loaded malware files into conversations that can write data to the registry, install DLL files, and potentially allow a hacker to take over someone else’s computer."
One of the most creative ways hackers gain access is by redirecting users to a spoofed login page through a phony Zoom or Teams meeting link, merely another way hackers are getting smarter, and more targeted with attacks.
"Once in, a malicious user can access privileged financial data and intellectual property - they can wreak havoc with fake messages, deleting or modifying files, or by harassing innocent users."
Would-be hackers can even listen to calls and chats in ways that Williams said: "amount to cyber espionage."
So Many Possibilities are on the Table
Mitigating a potential hack of any UCC system is possible. To avoid data leakage, denial of service, vulnerable credentials, cross-site scripting, and vulnerable APIs: ongoing education is a must, Williams told me.
But what about the lesser-known ways? According to Williams, many new and creative ways of hacking are only (now being) discovered. In Microsoft Teams alone, researchers have found spoofed URLs, the Microsoft Teams GIFShell attack (yes, it's exactly what it sounds like), and unencrypted authentication tokens.
Take recording a meeting from a third-party device, like an employee phone - believe it or not, it is more common than you might think. And Williams said; that alone can leave a company more exposed.
"Things people don’t think about include; having employees record Teams or Zoom sessions with their mobile devices for meetings that are not supposed to get recorded."
Willams shared that he knows of at least one instance where an employee got fired for this. "The employer claimed that action violated state laws."
Employees leveraging UC sessions for personal purposes that violate the law (think pornography or gambling) could be breaking state, local, or federal laws. And participants who display things in the background that violate social norms or reveal health-related matters (could) subject a company to HIPAA exposure - according to Williams.
But Vendor Responsibility Only Goes so Far
On vendor responsibility, it turns out that they only share part of the responsibility for ensuring hacks don't happen. But that - only goes so far. For starters, there are contractual limitations on what the vendors warrant. "That said, vendors (really) could do a much better job of educating their customers about security and privacy risks, " Williams remarked.
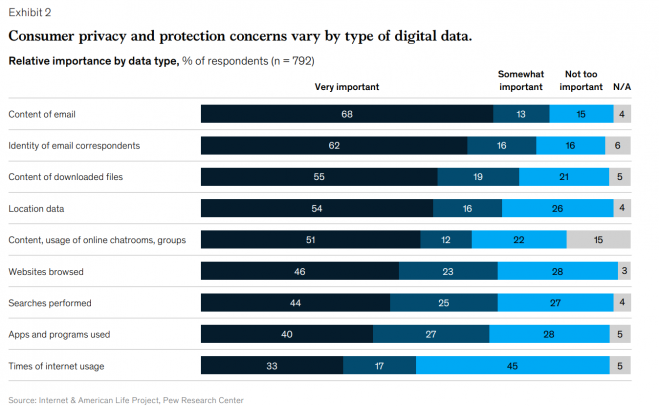
Cyber Security in a Digital Era, McKinsey, 2020
Here is where that shared responsibility comes into play, "however;" Williams said:
"It is 100% certain that customers need to do their due diligence on UC platform security – you cannot rely on the vendor to provide a secure environment."
So, it is a shared endeavor - at least it seems. But everyone ALWAYS says educate users, and that never seems to suffice. Williams agrees, telling me, that most enterprises have a UC team that manages product implementation and security, adding:
"That team should be challenged periodically by their internal CISO team tasked with cybersecurity diligence."
When it is all said and done: it is a shared responsibility to train users about UC security. It can be via email bulletins, which Williams said he sees most commonly, or as part of the employee’s annual cybersecurity training.
Stay tuned for the latest UCC news, insights, and analyses here on GetVoIP News.



