Modern VoIP solutions require several important steps to ensure high-quality calls. This includes performing tasks like disabling SIP ALG and purchasing a router that’s optimized for voice over internet protocol (VoIP) connections. Another step you can take is to incorporate a session border controller, which adds extra security to your calls over your phone system as well as data transfers.
What is a Session Border Controller?
A session border controller is like a firewall specifically designed for VoIP. It’s a hardware device or a software application that governs call admission to a network topology at the border. In this instance, the border refers to the space where the private network meets the public Internet. As part of controlling the border, the system filters calls, manages bandwidth, and protects against malware and viruses.
Essentially, a border controller on your network will control how calls are started, conducted, and terminated – and all the necessary media streams and data transfer to allow calls to occur. A session border controller will act as a firewall for your VoIP network, ensuring every call occurs properly and is protected along the way to its destination. These systems are generally deployed with all SIP networks.
In this context, a session is basically a call, but a border controller also governs other real-time video or data communication during your session initiation protocol calls. In some ways, a session controller is different from a traditional firewall. It looks at packets and grants them admission to the private IP network by opening up a port for data to go through or denies access and deletes the packets.
Voice and media traffic requires more open ports, and that leaves the network open to VoIP security vulnerabilities. The controller monitors the traffic to make sure that voice and other important traffic gets through, but malware does not. Also, whereas a firewall is designed to manage larger packets, an SBC is designed to secure the transmission of the much smaller VoIP packets since traditional firewalls sometimes miss these.
How a Session Border Controller Works
An SBC acts as a router or a firewall and sets up between the business’ network and the service provider’s network. It can be configured for a vast number of users and will differ for almost every business depending on what is considered more crucial.
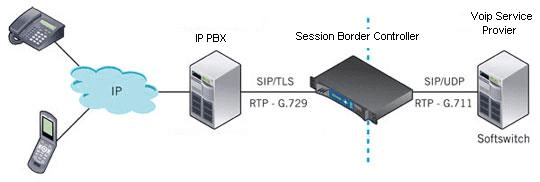
1. Security for Your Calls
At the most basic level, every SBC acts in a similar fashion. Just as a firewall or router, the controller will act as the gatekeeper for your network. Sitting at the “border of the network,” an SBC will monitor all phone calls or sessions. Along with monitoring each connection, a controller determines and allows only authorized sessions to occur. Sessions also include other media streams of data like video conferencing or webinars. With one of these interworking systems, only authorized information is connected and transferred through the network to help keep unwanted traffic out.
Session controllers also utilize call limiting so that there is limited traffic through active connections. Toll fraud happens when scammers generate fraudulent international calls on a connection with an open port. These usually happen in high volumes to “premium-rate numbers,” and the owner of the connection pays the bill. This kind of fraud is on the rise, so having a system to limit available bandwidth will prevent fraudsters from using or even selling access control to your trunks.
This narrowed port availability also prevents external access from unauthorized traffic, which reduces the chance of denial of service (DDOS) and spam over IP telephony (SPIT) attacks. DOS and other malicious attacks have increased by 16% since 2018, so reducing the number of available ports for access is critical.
2. Prioritization and Quality of Service (QoS) Management
An SBC monitors the quality of service status for every session to ensure that calls are lag or jitter-free. Data passes through and transfers without any interruptions or packet loss, as well as prioritizing different services and calls. For example, emergency calls placed on the network will receive a higher priority than standard calls to ensure they are completed with the highest QoS. These help with resource allocation on your network elements as well as rate limit to prevent bandwidth hogging.
Fault tolerance, which is another key feature, ensures 99.999% uptime for networks because of redundancy. Controller intra-chassis redundancy allows for a single unit to have multiple internal instances so that, when a session experiences a fault, the other instances pick up the slack. Additionally, single units work in tandem with other hardware or software on your network to ensure that there’s redundancy.
3. Protocol Translation and Connectivity
An SBC can help bridge the gap between multiple VoIP connections on different service provider networks. If your business is not only using a trunking service, but also general SIP-based or even legacy PSTN systems, an SBC can provide protocol translation. In fact, it can even act as a SIP to WebRTC gateway.
These allow for Network Address Translator (NAT) transversal and Ipv4 to Ipv6 conversions. NAT transversal is critical for peer-to-peer file sharing and voice since it establishes a tunnel between two devices through the network layer. NATs are designed to help networks overcome a limited number of IP version 4 private addresses. Modern session initiation protocol connections have a tendency to ignore NATs, and as a result, the SBC is needed to create the connection.
SBC also helps maintain connections across gateways or when converting IP protocol version 4 to version 6. This is important because version 6 is more VoIP-friendly and provides an infinite number of IP addresses when compared to IPv4. This makes the router’s job of making connections easier, and the SBC serves as an interface for making calls through the NAT.
How to Deploy an SBC
There are several different places an SBC may be placed:
- At the border between a telecom provider and the customer. This is the most common place you can find one.
- On the border of two different providers that have a peering agreement, which is called a network-to-network interface.
- Within a provider that offers virtual private networks. The SBC takes care of call routing within each VPN.
- Within a private network. If two high-bandwidth sites are linked by a low-bandwidth backbone, the SBC ensures the backbone is not overwhelmed by voice traffic.
Session border controllers grow with the size of the business. The hardware for an SBC made to handle a dozen calls can be around $2000, but enterprise SBC is made to handle thousands of calls and costs tens of thousands of dollars. It should come as no surprise that the market for SBCs is a hotly contested one, with major names in hardware putting out white papers on the importance of standard and enterprise session border controllers.
Security is often a major concern when it comes to networking for most businesses, especially an enterprise. Even when deploying a cloud PBX or SIP network to handle your real-time communications, security is a high concern because transferred voice data can be intercepted and heard by unauthorized ears. This is also the case with file transfers or text sent using unified communications tools.
When looking to protect your network during SIP calling, hardware or software network firewalls should act as a gatekeeper for that network. On top of that, a border controller helps lock down any and all information passing through your phone calls.
Understanding Session Border Controllers
When deploying a voice over internet solution an SBC is something you will never have to worry about, especially with hosted deployments. This is because everything is handled on the provider’s back end, so your business won’t have any real contact with the network, data centers, or any sort of SBC hardware or software. However, for an on-premise solution, place one at both ends of the enterprise network.

For any security-conscious business, it’s beneficial to understand how a session border controller secures your VoIP calls to make the best decision when looking for a new solution.
A Solution to NAT Troubles
Often, a business runs into trouble with Network Address Translation or NAT. This is a method of reusing IP addresses for multiple connections. Since there are a limited number of IP addresses with our current IPv4, NAT is necessary to allow a single device to act as a gatekeeper between the local network and the internet.
With NAT, only one IP address is required for the entire network of computers. Of course, this is just one use of NAT to help improve the security of a network. In practice, NAT settings often confuse networks and make it impossible for connections from the public internet to reach the end-user. However, these are often utilized to solve any NAT traversal issues.
With the SBC acting as the public connection of the user on that network, connections will always have a path to interconnect through the SBC to the user. This replaces the act of searching for a specific user with a generic IP address for the entire network.
Virtual Session Border Controllers
Another option besides the hardware device is the cloud-hosted and optimized Virtual border controller. SBC with virtualization is installed on a network machine and delivers the same functions as a hardware counterpart would.
The benefits of virtual SBC over on-premise hardware echoes the general benefits of a cloud-deployed solution. Simply put, because everything is hosted, and therefore handled on the back end of the cloud by the provider, there is no need for any hardware devices outside of IP phones (VoIP phones) and computers. Since it’s all in the cloud, the protection has great scalability. In fact, it can even be set as an automated function.
Should Your Network Employ an SBC?
Whether or not your business finds it necessary to incorporate an SBC into your voice solution depends on a number of factors. Not only that, but your business priorities will help determine if the controller is utilized and configured for your needs.
If your provider is already utilizing a border controller, it’s a good idea to complement your network with a local or virtualized SBC as well. If you prefer to avoid additional hardware concerns and costs, a Virtual SBC can suffice. If security is considered to be of high concern for your business, then a session border controller is critical in ensuring the highest level of security for your network.
Want more info on how to protect your valuable SIP trunks? Check out our guides on the subject; we also walk you through some of the top providers and tell you about the pros and cons of each.



