NAT is implemented in all routers, and sometimes again in the service provider network. More than 90% of mobile and wired devices access broadband networks using private IP addresses. These private IP addresses must be mapped into an address format that can access and be accessed by the public internet. NAT, or Network Address Translation, maps these addresses so private and public networks can interact.
What is it?
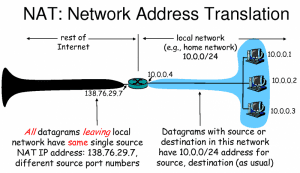
Network Address Translation is used by any device, like a router or firewall, that goes between an internal network (LAN) and an external network (The Internet). Local IP addresses, such as 192.168.1.1, 192.168.1.2, and so on, are, to the outside world, being sent to one IP address, which the router directs, and the firewall protects. In order to get to and from the local network, the data packets must be translated from the external IP address to the internal IP addresses, and vice versa. This translation is called NAT transversal. NAT has the secondary benefit of having each network have its own IP address rather than each device having its own unique IP address, which extends the number of available IP addresses. NAT was developed by Cisco.
How it Works?
NAT maps all of the private IP addresses on a home network for the single IP address that is provided by the IS. Packets coming from the external network are translated to the correct IP address within the network. Packets going out from the internal network to the Internet are also changed. The header of the packet is changed to look like they came from the device running NAT, rather than from the IP address of the device.
Type of NAT:
- Dynamic NAT: Maps an unregistered IP address to a registered IP address by selecting from a group of registered IP addresses.
- STATIC NAT: Maps an unregistered IP address to a registered IP address on a one-to-one basis
- PAT/Port Address Translation: Also called overloading, this is a form of dynamic NAT that maps multiple unregistered IP addresses to a single registered IP address by opening up different ports.
Types of NAT traversal
Session Border Controller: This method is specialized toward VoIP. One of the many functions of a session border controller (SBC) is to allow different parts of the network to communicate to each other, including NAT traversal. The SBC itself is found at the border between two networks, and controls what can and cannot go through. VoIP traffic is a little different than regular web traffic, so SBC ensures that the VoIP traffic is reassembled in the right order, and that it gets priority over other traffic.
- STUN (Session Traversal Utilities for NAT) is a simple query and response. (Q: May I please come in and deliver these important messages? A: Yes/No)
- TURN (Traversal Using Relays Around NAT) uses a third party server to relay messages between two clients where a firewall blocks all P2P communication.
- UPnP (Universal Plug and Play) is a set of protocols that permits devices to discover each other’s presence even within a private network.
- ICE (Interactive Connectivity Establishment) figures out which of the previously mentioned protocols works best, and uses that.
Security
NAT is not, strictly speaking, a security feature. By itself, NAT does not provide the features of a firewall, but it is often used on servers that have firewall and antivirus software. When using static NAT, the inside host is exposed at all times. Static NAT is designed for when a device needs to be accessible from outside the network. While this is good when under controlled situations, it leaves the device vulnerable to attack.
Examples of NAT software
Professional NAT software:
- Eyeball Networks - AnyFirewall Engine Software helps providers overcome NAT traversal issues.
- NAT32 Second Edition – Makes web browsing safe and fast. Includes a security feature called a “honeypot” that changes the default given address for added security.
- Pwnat – Prounounced “Poe-nat,” this controversial NAT tool was created by the same person who made the Samy MySpace worm. Designed to create a tunnel between two computers on separate networks over the internet without the need for port forwarding, this NAT tool gives users a way to bypass restrictions that you would otherwise need administrative access for.
Free/Personal software that uses NAT traversal:
- ReverseNAT – If your host is behind a NAT, it cannot accept an incoming connection from computers outside it. Accept incoming connections from computers that are outside your NAT with this software
- SopCast 3.8.3 – Build your own TV station using the power of P2P technology. Stream over P2P (SoP) gives the user a selection of free channels. It has firewall and NAT traversal for pass 90% of P2P barriers.
NAT operates at the network layer 3, which is the same layer routers work at. While NAT is not a traditional firewall, it does sit between an internal network and an external network, and assigns traffic to the proper place. In most cases, it dynamically maps unregistered IP addresses to registered IP