As more businesses switch to VoIP and competition between providers stiffens, businesses reap the rewards with more powerful and advanced technology for their money. The newest crop of Cisco VoIP phones is no exception. We’re taking a closer look at our favorite cisco business phone models for every business, niche, and budget.
Cisco sets the industry standard, driving innovation in areas such as Artificial Intelligence with their AI-powered Spark Assistant. They bring decades of research and experience to all of their products.
By staying on the cutting edge of technology while also keeping the user experience in mind, Cisco IP phones are the most popular and highest quality phones in the market.
How Do Business VoIP Phones Work?
Business VoIP phones are designed to work within a business VoIP communications system. They are designed to operate using the internet as opposed to the Public Telephone Switched Network (PTSN).
VoIP phones beat landline phones in several ways. The main advantage is a drastically reduced phone bill. When it comes to international calls, VoIP calls are a fraction of the cost of traditional telephony. This has made the option the best choice for several industries and why you’ll find VoIP in hotels around the world.
Business VoIP phones allow users to be completely mobile, accessible from any device that has internet access. VoIP phones allow for free-flowing communication across multiple channels and devices. They’re built for keeping valuable data secure, conveniently stored, and readily available.
Another advantage of a Cisco VoIP phone system is the seemingly endless list of available features. This includes but isn’t limited to IVR, auto attendants, call recording, video chat, and conferencing. The innovative features like digital whiteboards and video chat that make VoIP a great option for schools.
Cisco makes some of the top IP phones, designed to make all of these features easy and intuitive for users.
When to Upgrade Your Existing VoIP Phones
You need to consider updates to both hardware and software when setting up a new VoIP system. If you’re using a Cisco VoIP phone system and Cisco phones, you probably know that the software is periodically updated automatically. Cisco phone hardware is as robust and durable as the software, so phone system upgrades need not be frequent.
Some scenarios will call for a hardware upgrade. If your business recently taken on several new employees or is looking to scale up, it could be time to upgrade.
A new VoIP business phone system could help you if you recently started traveling more or working remotely. The same goes for if you want your employees to be able to work from home.
Consider whether your phones could better serve your business. For example, there are advanced business features like video conferencing that could give you a much-needed edge. If this is the case, it may be time for an upgrade.
Essential Features of the Best Cisco VoIP Phones
Cisco has a wide variety of offerings when it comes to VoIP phones. When choosing our favorite Cisco IP phones, the first thing we looked for was a high-quality sound. Whether using Bluetooth, handset, speakerphone or even video chat, clear audio is an absolute must and expected from the kind of quality telepresence Cisco has always offered.
We also looked for high-quality features such as programmable keys, a Gigabit switch and key expansion. Further, we judged whether these features were offered at a fair price. We want to determine if these phones provide users real value.
We also looked at whether a phone would last with wear and tear as well as personnel changes and rapid business growth in the years to come.
In our Cisco phone comparison, we also judged phones based on how intuitive and easy to use they were. We know it’s important for staff members to find what they need when they need it.
Top 7 Cisco VoIP Phones
Almost any Cisco wireless VoIP phone is going to offer great value for your business, but we believe that the following phones go above and beyond.
Cisco CP-8861

The Cisco IP Phone CP-8861 comes with 5 Lines, WiFI support, integrated Bluetooth, and a USB port with fast charging capability. It includes wideband audio and echo cancellation for voice clarity as well as a 10/100/1000 internet switch for exceptional speed.
The sleek, ergonomic design of this phone makes it very user-friendly. The high-resolution color display makes it quick and easy to scroll through a directory or voicemail list. The powerful technology and considered design of this phone make it a simple and impressive choice.
As part of the Cisco 8800 series, the 8861 comes with some very cutting edge features including Cisco’s Intelligent Proximity for Mobile Voice, which is an entire suite of features that activates when users bring mobile devices close to any voice and/or collaboration endpoints in the system.
Best For
The 8861 is an ideal phone for knowledge workers and remote workers across industries and businesses of all sizes due to its flexibility between desk phone and mobile devices. Users can even move the audio path during an active mobile call over to the IP Phone 8861 and take advantage of its superior audio, for example, to share a mobile conversation with a colleague. Despite the flexibility of the 8861, it is a highly secure phone, using encrypted voice.
Overall Comparison
The only downsides to this phone are a lack of video capabilities and a price that is definitely on the high end.
| Pros | Cons | Features | Rating | Price |
|
|
|
5/5 stars | $325 |
Cisco 8845 VoIP Phone

If you are looking for a high-quality HD video phone that also gives you access to the most cutting edge unified communication features, this is the one. It also includes a high level of security, this phone is for you.
Like the 8861, the 8845 comes with Cisco’s Intelligent Proximity for Mobile Voice allowing for easy transitions between a desk and mobile phone. Like the 8861, the 8845 has a design that is attractive, ergonomic and intuitive.
Both the sound quality and video quality of this phone are top-notch. The video is 720p HD with H.264 advanced video coding. The sound is crystal clear thanks to wideband audio and a full-duplex speakerphone.

Best For
The Cisco 8845 is ideal for knowledge workers, administrative staff and executives across industries. It allows users to easily communicate across multiple channels and take advantage of hundreds of advanced Cisco features with ease.
Overall Comparison
The only real downside to this phone is the high price tag. You will probably want to save this phone for those executives that need to be in constant communication.
| Pros | Cons | Features | Rating | Price |
|
|
|
4/5 stars | $250 |
Cisco CP-8865 IP Phone

Combining the high-def Video conferencing from the 8845 and all the connection options from the 8861, this flagship phone works well everywhere. It’s great for open workspaces, large conference rooms, executive offices, and actively mobile users within a campus.
The 8865 is meant to be a successor to the 9951/9971 models. The only difference between the 8865 and the 8845 is here we see more modular compatibility. It has wi-fi and the ability to add KEM accessories or any other hard wired connection standard to the 8861.
Considering the moderate price difference between this phone and the 8845, this phone likely offers superior value.

Best For
The Cisco 8865 is best for executive staff and advanced IT/AV workers. For anyone needing to install a phone without knowing ahead of time what accessories will be required, this is the clear choice. For those situations where you need to be able to answer “yes” to a request for a given feature rather than “wait”, this is the model you will want to build from.
Overall Comparison
Given the feature set, this model should be priced much higher than the 8845 in our estimates but often can be found priced lower due to the 8845’s popularity.
| Pros | Cons | Features | Rating | Price |
|
|
|
5/5 stars | $300 |
Cisco CP-7841 IP Phone

The Cisco 7841 can be considered a sibling of the 7861. Without a dedicated line panel, this form factor unit can manage up to four lines simultaneously before maxing out the interface.
For those requiring a 10/100/1000 integral switch, this will be your only option in this series according to the Cisco website.
This model does include a pleasant white backlight for its anti-glare graphical model chrome display. Under the hood, we see the advanced Cisco connectivity features shared by all the 7800 series including multi-call, per line graphics and mobile remote access. This device has an auxiliary port so your call center reps will be at home if part of a fleet perhaps with a 7661 unit at the helm.
Aesthetically this hardware comes in your standard charcoal or white.

Best For
This 4-line model is well suited for administrative staff, managers, and customer care agents, or anyone with moderate-to-active voice communications needs.
Overall Comparison
This mid-level phone has a limited interface but can manage four lines. It's perfect for a small- to medium-sized business with limited routing or conferencing needs.
| Pros | Cons | Features | Rating | Price |
|
|
|
3/5 stars | $365 |
Cisco 7861 IP Phone

The Cisco 7861 IP Phone is a great choice for your general business VoIP communications needs. It combines modern features, security, and audio clarity with state of the art tech enhancing the speakerphone experience.
The 7800 series is a great VoIP option for large businesses and small ones alike and will even be up to the task for most front desk reception and call rerouting. This phone lacks some of the flashier accessories and features such as color screens and ultra compatibility/connectivity. However, it makes up for that in straightforward task-oriented convenience.
The screen is a standard anti-glare monochrome with a pleasant white backlight and a straightforward user interface. The menus and quick access to caller ID and other more advanced menu features such as phone book and call log access are intuitive to find.
The security on this device is up to date and for those wanting to deploy this unit with pre-existing infrastructure. It's backward compatible with the Cisco brand but remote cloud delivery which will come in handy if your business is expecting to scale.
One surprising caveat is the lack of 10/100/1000 integral switch support according to the Cisco website. This won't be a problem for most but it might be something to keep an eye on if 1000 switch compatibility is a must-have.

Best For
The 7861 offers a lot of features that have come to be expected in high volume call situations which makes this phone a popular choice for team managers, switchboard operators, security offices and reception desks. Advanced features such as 4 programmable soft keys and the ability to manage up to 16 individual lines at the press of a button make this the flagship of the 7800 series.
Overall Comparison
If mobile remote access without a VPN is important to you, this phone is a great choice. The Cisco expressway gives flexibility both on campus or in the cloud using Cisco WebEx. This is your ideal device for those managing up to 16 lines at a time without being overwhelmed by touch screen options or alter advanced features.
| Pros | Cons | Features | Rating | Price |
|
|
|
3.5/5 stars | $395 |
Cisco 6901 Unified IP Phone

The Cisco 6901 VoIP phone is likely the simplest modern IP phone that Cisco deploys. It's affordable, reliable, has a trim footprint, and is wall mountable.
The hardware is completely straightforward and easy to use. This is a handset only device and best for home or shared spaces.
The 6901 is not recommended for security checkpoints because of the lack of caller ID. However, other great features that are standard for IP phones are present without complicating the user interface.

Best For
If you need phones for lobbies, cafeterias, hallways, elevators, conference centers, guest rooms, dorm rooms, this is the one for you. Office workers who only need a simple, intuitive VoIP phone with no frills will appreciate this model as well.
Overall Comparison
With features like adjustable ringtones, LED, message indicators, and call waiting, it has more than meets the eye. This is a lightweight handset that will be easy on the eyes mounted on the wall or sitting on a desk.
| Pros | Cons | Features | Rating | Price |
|
|
|
4/5 stars | $50-$70 |
Cisco 3905 Unified SIP Phone

The Cisco 3905 is excellent as an entry-level VoIP endpoint system. It is ideal for making and receiving calls to hallways, lobbies, general use laboratories, classrooms, dormitories, cafeterias, conference centers, security endpoint locations, etc.
This phone shines in shared spaces where minimal VoIP communication services are used. It is a perfect phone to mount on the wall.
The 3905 is a simple, easy to use and straightforward fleet phone with a monochrome display featuring standard caller ID, call history and phone information. It is small and lightweight with a standard 12 digit dial pad. There are no distracting programmable buttons on this phone.
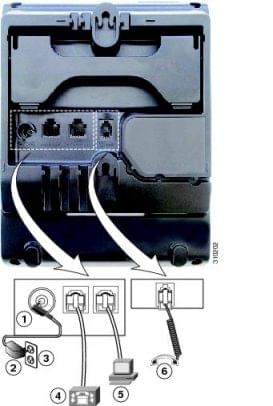
Best For
This one is great for scaling call centers and businesses just starting to deploy a VoIP system. If you don’t need video conferencing, this could fill out your fleet while more expensive models line the desks of executives and managers.
Overall Comparison
This is a standard-issue, minimalistic IP phone great for shared spaces. It's inexpensive and durable with a small footprint. Receptionists and administrative staff that experience light to moderate call volume will find this suits their needs for a basic SIP phone that is easy to use.
| Pros | Cons | Features | Rating | Price |
|
|
|
5/5 stars | $70-80 |
Cisco’s Business VoIP Phones Are the Industry Standard
When it comes to implementing business VoIP phones at your office or call center, Cisco business phones are the way to go. However, you must consider the current budget and growth potential of your business before you invest.
If you’re thinking about investing in a new provider with your Cisco business phone system, we have a breakdown covering every major business VoIP provider.



