Though you might feel frustrated with your employees scrolling through social media or texting friends at the office, as long as they’re using their personal smartphones or tablets, it’s not a major threat to business security…right?
If your employees also use their personal devices to check work emails, make calls from the company VoIP app, edit project files, or access client information, then yes–your business’s data and applications are facing a significant security risk.
A BYOD policy protects business and client sensitive information, ensures you’re in line with industry regulations and allows your employees to keep using their favorite devices to get work done–whether they’re in the office or fully remote.
Read on to learn what BYOD means, how to develop a strong BYOD policy, and the pros and cons of hopping on the “Bring Your Own Everything” bandwagon.
What is BYOD?
BYOD (Bring Your Own Device) is a policy permitting remote or in-office employees to access a company’s business software, files, or any other work-related programs and information on their personal devices.
BYOD devices are owned by the employees–not the businesses they work for–and are used for both personal and professional activities.
The most common BYOD devices include personal laptops, desktop computers, Apple iOS and Android smartphones, and tablets. However, the cultural acceptance of the remote workforce expanded the borders of the “Bring Your Own” universe.
“BYOX,” an umbrella term encompassing all “Bring Your Own” possibilities, includes BYOD and newer BYO trends and technologies like:
- BYOA (Bring Your Own App)
- BYOC (Bring Your Own Cloud)
- BYOT (Bring Your Own Technology/Tools)
- BYOS (Bring Your Own Storage)
- BYOW (Bring Your Own Wearables)
- BYOE (Bring Your Own Encryption or Bring Your Own Equipment)
Though convenient for team members and an excellent cost-saving opportunity for business owners, the BYO revolution adds many new variables into the mix–especially regarding security, IT, employee monitoring, and compliance.
It’s easy to see how, without a set of rules and regulations in place, BYOD could lead to data breaches, compromised client information, cyber attacks, and other security issues that damage your business’s reputation and cost you millions in penalties.
That’s why it’s so important to have a strong BYOD policy in place.
How Does a BYOD Policy Work?
A BYOD Policy is a set of company-wide rules that govern how employees can use their own devices (and all other forms of personal technology) to access company data, applications, and networks.
A BYOD program outlines the security, privacy, and ethical standards employees agree to adhere to when using personal devices for any work-related activity. It also clarifies the ways a company can monitor, access, update, manage, or revoke access to employee personal devices.
Note that, depending on the specifics of the policy in place, companies may remotely wipe both personal and business data on a personal device, or simply revoke the device’s ability to access the company network/applications.
This brings us to one of the more difficult aspects of a BYOD policy: respecting an employee’s right to privacy while maintaining regulatory compliance, meeting security standards, and ensuring employees engage in acceptable activity when using their devices for work-related purposes.
BYOD blurs the line between an employee’s personal and professional life–but there are solutions.
BYOD Security, Device Management, and Access Control
Before you develop your own BYOD policy, you need to determine how you and your IT department will manage employee devices, the software and security solutions you’ll use to do it, and your strategy for compartmentalizing personal and professional device activity.
Here, we’ll outline some of the most popular–and secure–BYOD tools and device management strategies.
Cloud Communications Software
Luckily, today’s cloud communication and collaboration tools simplify the BYOD process.
Cloud-based business software (SaaS) exists within its own virtual world–providing users access via downloadable desktop and mobile cloud applications and/or no-download, browser-based applications.
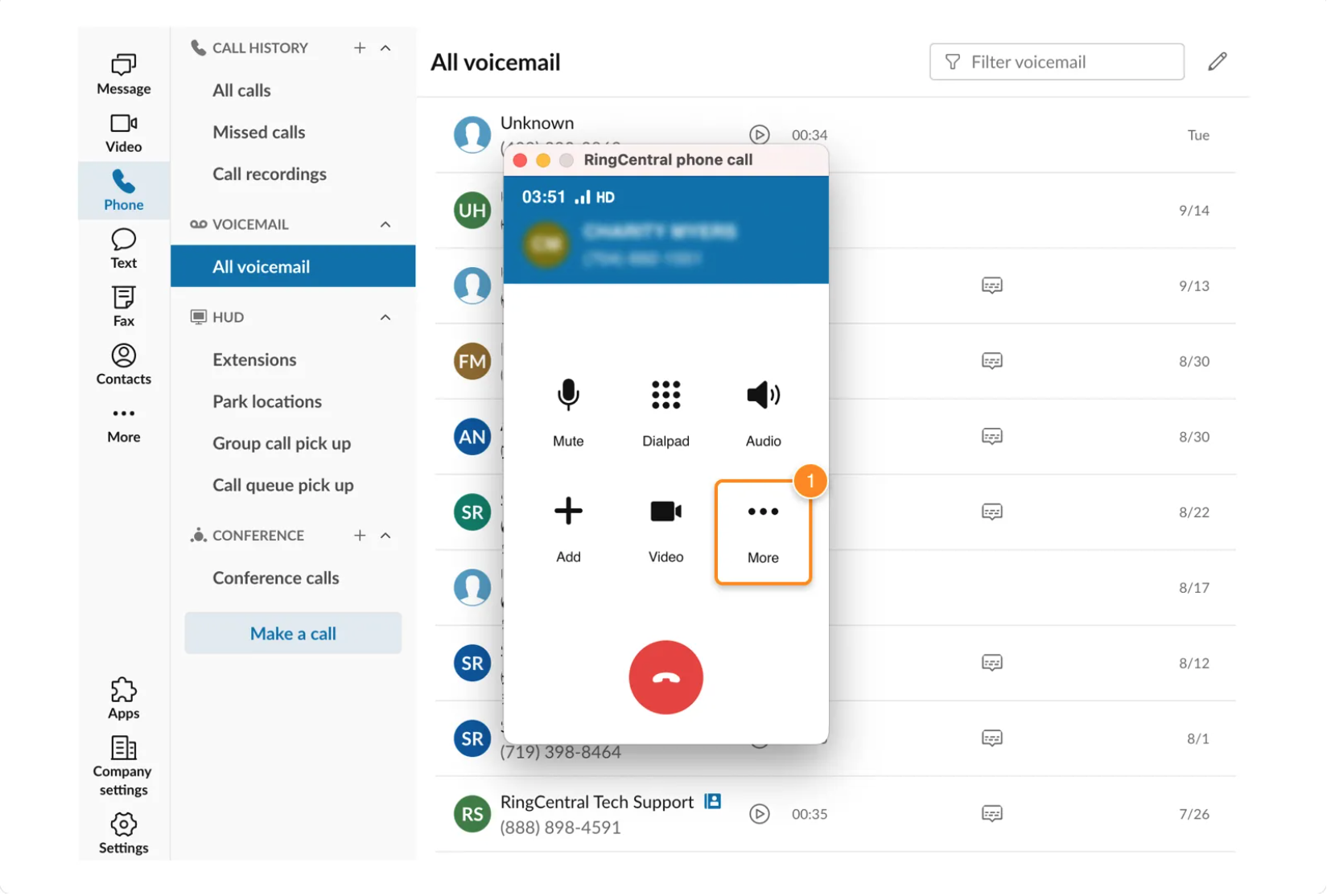
The desktop version of the cloud-based RingCentral phone system
These cloud platforms offer high-level BYOD compatibility, working with many different desktop and mobile devices, smartphone makes and models, operating systems, and web browsers.
This means employees are able to access a secure virtual desktop environment on their own devices. Cloud platforms “containerize” personal and professional activity on employee devices–activating a “work-only” universe as soon as employees log into the company network.
Containerization prevents cross-pollination between personal and business email addresses, contacts, files, web browsers, and all other data.
In most cases, employees can’t even access their personal apps when logged into the company application–but when they log out, the phone functions just like a personal device.
It lets admins and IT teams monitor employee activity, control access, and more–but only when team members use the company network.
Popular cloud-based business tools with BYOD configuration include business phone systems, contact center software, video conferencing apps, cloud storage solutions, team chat platforms, and more.
Mobile Device Management (MDM)
Mobile Device Management (MDM) is a BYOD security practice where employees agree to let their company access their personal devices to deploy and access business-owned software, device security and storage applications, and any additional business systems.
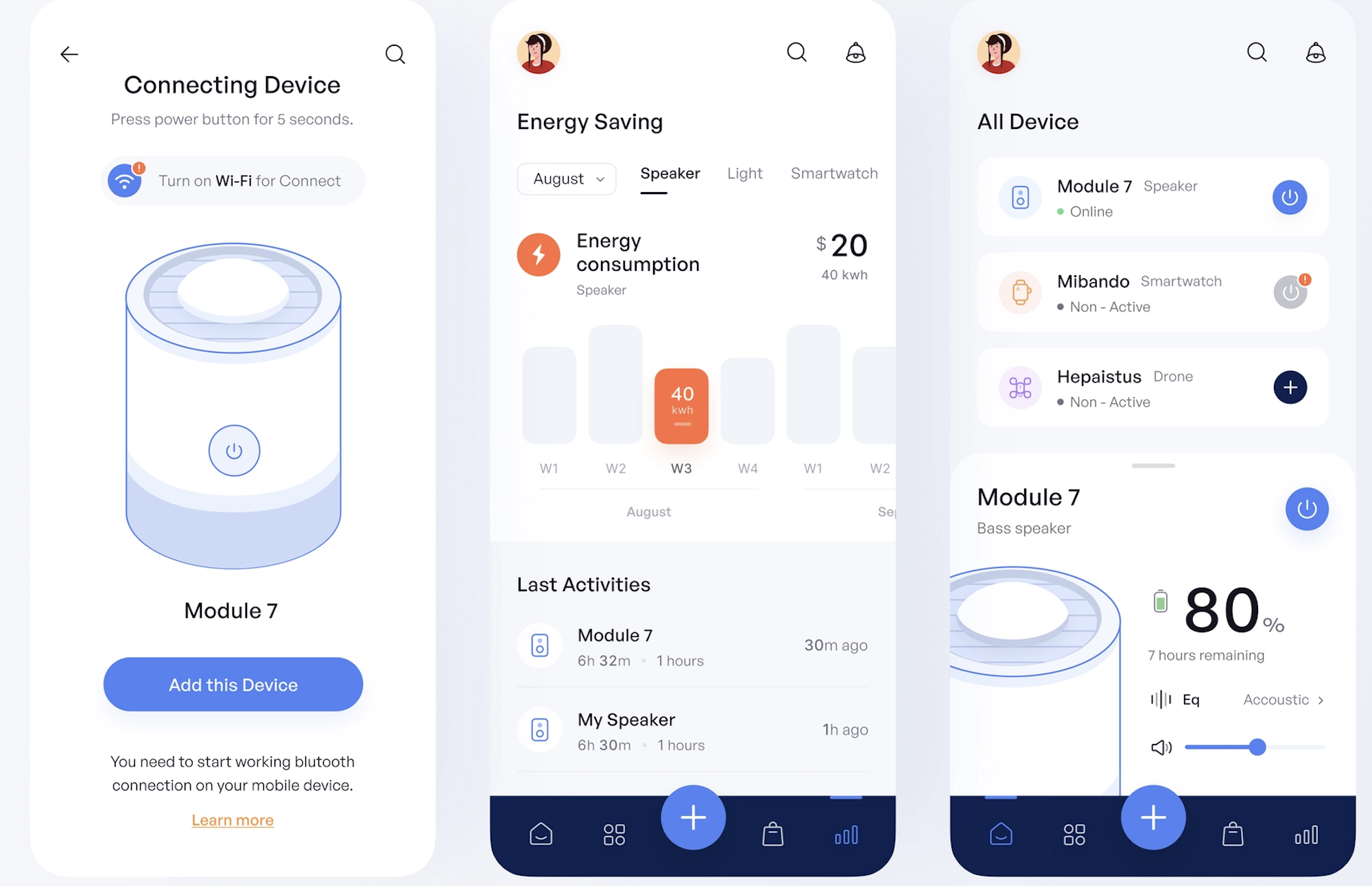
MDM software capabilities include monitoring all network-connected device activity. (Image Source)
MDM gives companies the ability to monitor remote employees within these downloaded applications only, ensuring security standards and use policies are met while employees access the company network. MDM grants IT teams access to employee personal devices, allowing them to install/configure/update software, regulate data storage, control the apps and websites employees access, monitor access and employee activity, and more.
Once the employee ends their connection to the company network, their device activity is no longer monitored.
Popular MDM solutions include:
- Kandji
- Miradore
- Informatica
- Rippling
- Jamf
Mobile Application Management (MAM)
Mobile Application Management is even more specific than MDM, as it only manages and monitors individual applications installed on an employee’s device.
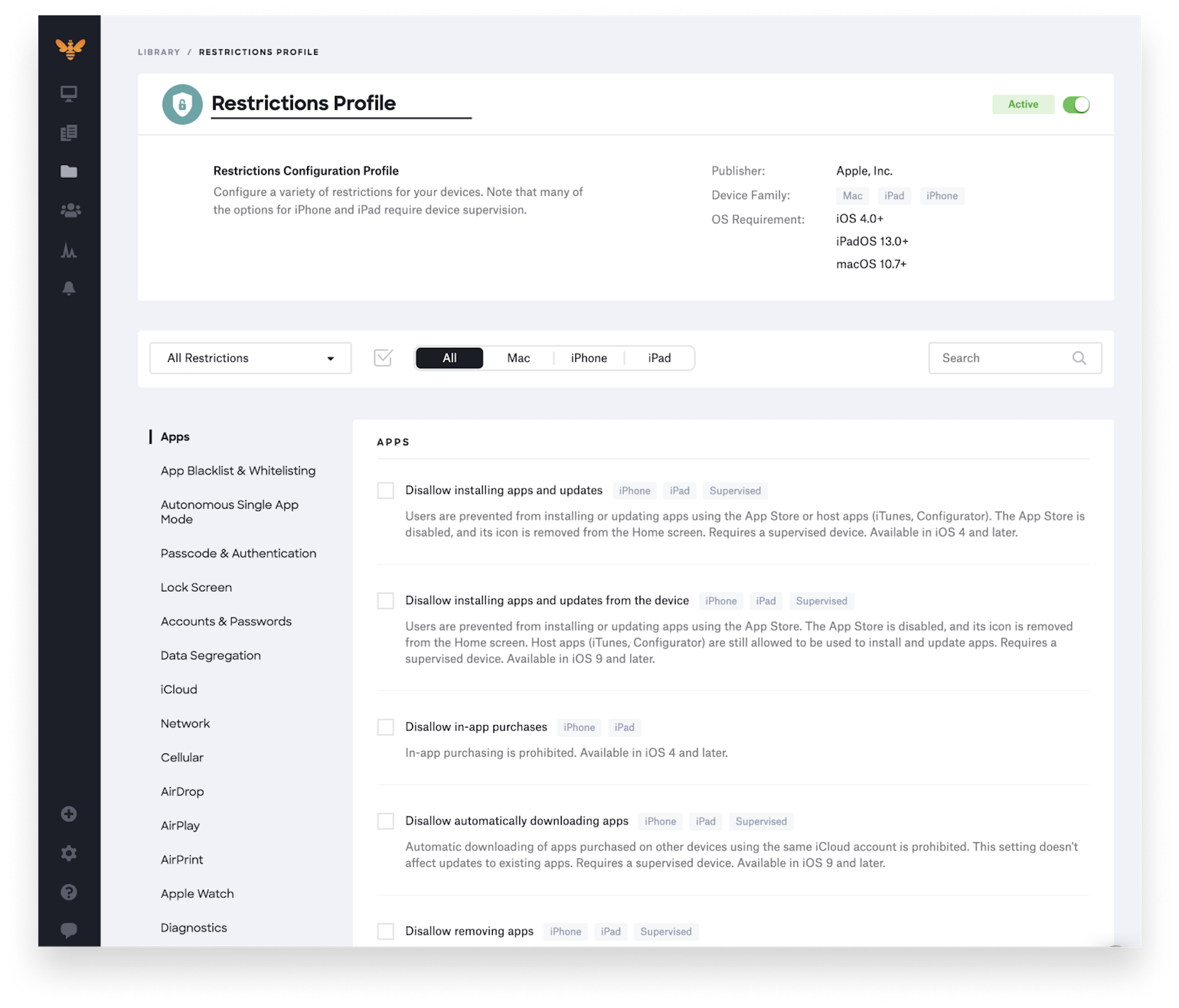
MDM and MAM platforms offer detailed configuration controls.
If the device is lost, or if the employee leaves the company, IT can simply lock them out of the app login or remotely delete the app from their phones. MAM also means employees don’t need to worry about their personal data, like photos or videos, being wiped.
Zero Trust
Zero Trust is a security strategy that requires any user–whether internal or external–attempting to access company networks/applications to be continuously authenticated, verified, and authorized throughout their interactions with a system.
“Zero Trust” assumes malicious intent and therefore takes a preventative approach to cybersecurity. No one can access the network or endpoints without continued verification.
The Zero Trust approach is especially valuable within the BYOD space, as it prevents anyone who can’t provide the correct authentication details–like hackers or even family members borrowing the device–from accessing any corporate data.
How to Develop Your Own BYOD Policy
Once you’ve determined how you’ll secure and monitor your employee’s personal devices, you’re ready to write your own BYOD policy.
All employees, including any short-term contractors granted limited remote access to company systems, should be required to sign the company BYOD policy.
Step One: Outline Acceptable Devices
The very first step in your BYOD policy development process should be to define which devices are and aren’t acceptable for employees to use for work tasks.
It’s not enough just to state the types of devices allowed.
You’ll also need to specify:
- Acceptable Operating Systems (macOS, Windows, Linux, etc.)
- The minimum required versions of accepted Operating Systems (macOS 13+above, etc.)
- Acceptable device models (iPhone 11+above, Windows 10+above, etc.)
When choosing eligible BYOD devices for your workplace, consider:
- Which Operating Systems and devices are compatible with the business software, security applications, and network monitoring/device management tools your business uses
- The level of cross-compatibility between acceptable devices
- If your IT team has the training/skillset to offer support for a proposed device/OS
- The standard security settings of each device/application/browser, etc.
- If the device offers end-to-end encryption
Step Two: Define Acceptable Use
Once you’ve outlined acceptable devices, you’ll need to define the Terms of Acceptable Use–the kinds of activities your employees can and cannot engage in when accessing the company network/business applications on personal devices.
This section should also define which third-party applications or websites should and should not be accessed/downloaded on the company network.
To make this step more manageable, some businesses opt to blacklist (block access to) certain websites, social networking platforms, or applications. Others businesses choose whitelisting, which blocks access to all websites or outside applications except those on a predetermined list.
Blacklisting and whitelisting are really only suitable for company-owned devices, or within company networks/applications that employees access on personal devices.
Terms of Acceptable Use should also:
- Outline which work-related applications/functions can be accessed on personal devices (work email, VPN network, CRM systems, team messaging apps, etc.)
- List which applications, social media platforms, websites, and types of activity cannot be conducted on personal devices when connected to company-owned devices, networks, or applications
- Application install control, including limiting access to app stores while connected to the corporate network
- Define the types of company-related data (if any) that can be stored on personal devices, the location and length of data storage, and data ownership
- Outline expectations regarding data sharing, copyrighted materials, password sharing, account access, etc.
- Forbid illegal activity, harassment, threats, intentional/malicious network interference or hacking, etc.
Step Three: Set Minimum Security Standards
Next, outline the minimum security standards your employees will need to follow when using their personal devices for work purposes.
An example of two-factor authentication from 8x8
Common security measures and standards to mention here include:
- Enabling two-factor authentication (2FA) or multi-factor authentication
- Enabling end-to-end encryption (E2EE)
- Requiring employees to download specific antivirus/anti-malware services not included within MDM/cloud communication applications
- Any industry-specific compliance regulations employees must adhere to (HIPAA, GDPR, PCI, etc.)
- The user authentication and identification process
- Regularly updating software, OS, etc.
- The process for reporting lost/stolen devices
- Password policies (specify minimum length/special character requirement, forbid using multiple passwords for the same account/saving passwords state how often passwords should be changed)
- Device auto-locking and automatic sign-out rules
Step Four: Cover Employee Privacy and Device Monitoring
This is the most important section of your BYOD policy, as it specifically outlines:
- Which security software, cloud communications applications, network monitoring, or mobile device/data management tools (if any) your company/IT team can access and download on employee devices
- The information and applications on employee devices that your company can and cannot access, store, update, install, remove, or monitor
- Your company’s process for random security audits and adherence monitoring
- The types of IT support your company will provide, alongside the right to configure employee devices to ensure network and application compatibility
- Any financial reimbursement your company will offer employees for device repair, upgrade, replacement, etc.
- The company’s responsibilities regarding the protection of personal data and an employee’s right to privacy
- The permissions/levels of access your employees have to the company network
Step Five: Address Liabilities+Define Consequences of Policy Violation
Your BYOD policy needs to clearly define the potential loss of data–and any other liabilities–employees could incur if their personal device is lost, stolen, or compromised in some way.
This section is essential, as it gives your business authorization to remotely wipe an employee’s personal device and protect sensitive data if needed.
If the device will be remotely wiped, specify if the employee will lose access to both personal and company data, or company data alone. State that backing up any personal data stored on personal devices is the sole responsibility of the employee, not of the company.
Outline the ways in which company systems/data will be removed from an employee’s personal device upon termination, a detected data breach, or end of employment.
Finally, clearly state the consequences of an employee’s failure to adhere to the standards/requirements outlined in the BYOD security policy.
The Pros and Cons of BYOD
The below pros and cons list highlights the major risks and benefits of BYOD, which we’ll explore in further detail.
| BYOD Pros | BYOD Cons |
| Significant cost savings for businesses | Increased security risks |
| No learning curve for employees | Can complicate IT support |
| Meets the needs of a remote, blended, and/or highly mobile work environment | Confusion over phone number ownership |
| Increased employee productivity and morale | Potential for employee pushback |
Pro: Significant Cost Savings
Research from Cisco perfectly illustrates the cost-saving benefits of BYOD.
The study found that implementing even a basic BYOD policy saves businesses about $350 per employee, per year on the costs of hardware, onboarding/training, IT support, and more.
A more complete BYOD policy can save companies up to $1300 per year, per employee.
Eliminating the need to purchase employee-owned devices can easily save companies thousands annually.
Con: Increased Security Risks
The biggest con of implementing a BYOD policy is that its convenience and cost-savings come with increased security vulnerabilities and risks.
Though avoiding every security threat or thwarting every cyber attack is impossible, knowing what to watch for can limit the risks of BYOD.
The most common BYOD security concerns include:
- Stolen or lost devices
- Unsecured public wifi networks
- Employees stealing or sharing data with malicious intent
- Regulatory non-compliance and resulting lawsuits/penalties
- Malware, ransomware, hacking, computer viruses, spyware, etc.
- Failure of employees to comply with BYOD policy and security standards (weak/shared passwords, failure to enable E2EE/2FA, failure to update devices, etc.)
- Honeypot/phishing/spoofing schemes
- Unsecure data transfers
Pro: No Device Learning Curve
Teaching team members how to use new software, updating them on HR policies, and providing professional development and continuing education is essential–but takes up valuable time.
Letting team members use devices they’re already familiar with and prefer eliminates training time and expenses and allows for smoother communication with clients and colleagues.
In addition to eliminating the learning curve, most people always opt to upgrade their own smartphones and personal devices before those they use for work. This means your company can benefit from the latest technology, functionalities, and security features–without having to pay for it.
Con: Can Complicate IT Support
While BYOD means companies no longer have to purchase devices for their employees, it also means your IT team will need to navigate multiple device types, manufacturers, models, and operating systems.
This lack of device uniformity can:
- Make internal cross-device communication difficult
- Force your IT department to familiarize themselves with numerous devices, their security standards, and how to install MDM/company networks on them
- Prevent access to a uniform set of features across devices (for example, not all busienss VoIP features are accessible on smartphones, but are on laptop computers)
- Make it difficult to keep up with differing OS updates, security breaches, etc.
- Rule out potential software (for monitoring or business communication) due to lack of compatibility
To combat these issues, narrow your list of accepted personal devices, look for software that’s compatible with the most popular devices your employees use, or just outsource IT support to the SaaS provider.
Pro: Supports A Remote and Mobile Workforce
Today’s remote/blended workforce demands business software that:
- Can be accessed from any location with an Internet connection
- Works with any device
- Is mobile/portable
- Enables flexible work hours
- Is consistent in functionality and interface across devices
- Automatically syncs activities and updates across channels, devices, locations, etc.
BYOD meets all these needs, and most SaaS platforms include BYOD onboarding and support in their monthly plans. Allowing employees to use multiple devices to access company networks and apps helps your team stay on schedule, in communication with each other, and in compliance with industry regulations.
Today’s workforce doesn’t just want to be able to work remotely–they expect businesses to offer them the option. Having a BYOD policy in place shows you’re in touch with employee needs.
Con: Phone Number Ownership Complications
Since BYOD lets employees use their own devices to communicate with clients, it can be difficult to understand who owns the business phone number connected to the personal device.
If an employee leaves the company, they’re not likely to “hand over” ownership of their phone number to your business.
And if clients call that employee after they’ve left?
You run the risk of losing their business.
Luckily, requiring all employees to contact clients through your business software applications/networks eliminates this confusion. That’s because cloud phone systems provide each user (employee) with their own unique phone number or user extension. Because your company owns the software license, it also owns all the employee phone numbers.
Pro: Increases Team Productivity and Morale
A Frost & Sullivan study found employees saved 58 minutes per work day by using their personal devices to complete work tasks.
The same study showed that granting employees access to their personal devices at work increased productivity levels by 34%, while a Jamf survey found nearly 70% of employees are more productive when working on their device of choice.
BYOD doesn’t just boost productivity–it also improves employee morale, which can lead to decreased turnover rates, higher employee satisfaction rates, and better overall employee performance.
The same Jamf survey referenced above found a whopping 77% of employees said they’re much more likely to stay with a company that let them choose and use their own devices–and 35% said that working on their preferred device made them proud of their workplace.
Con: Potential Employee Pushback
Employees may express concerns about potential privacy violations and feel uncomfortable signing a policy that allows their employer to monitor their activity on personal devices.
While these concerns are valid, the best way to address or avoid them is to involve your employees in the BYOD policy development process. Use device monitoring software or cloud phone apps that successfully containerize personal and professional device activity. Explain to employees that your goal isn’t to “snoop” on their devices, but to ensure that company data is protected.
To gain employee trust, your BYOD policy should clearly state that your company will never store, access, or share employee personal data. It should also clarify the apps, networks, and activity that will be monitored.
Finally, make sure to regularly review your BYOD policy, and offer employees continuing education regarding BYOD and privacy expectations.
BYOD FAQs
Below, we’ve answered some of the most common BYOD FAQS.



